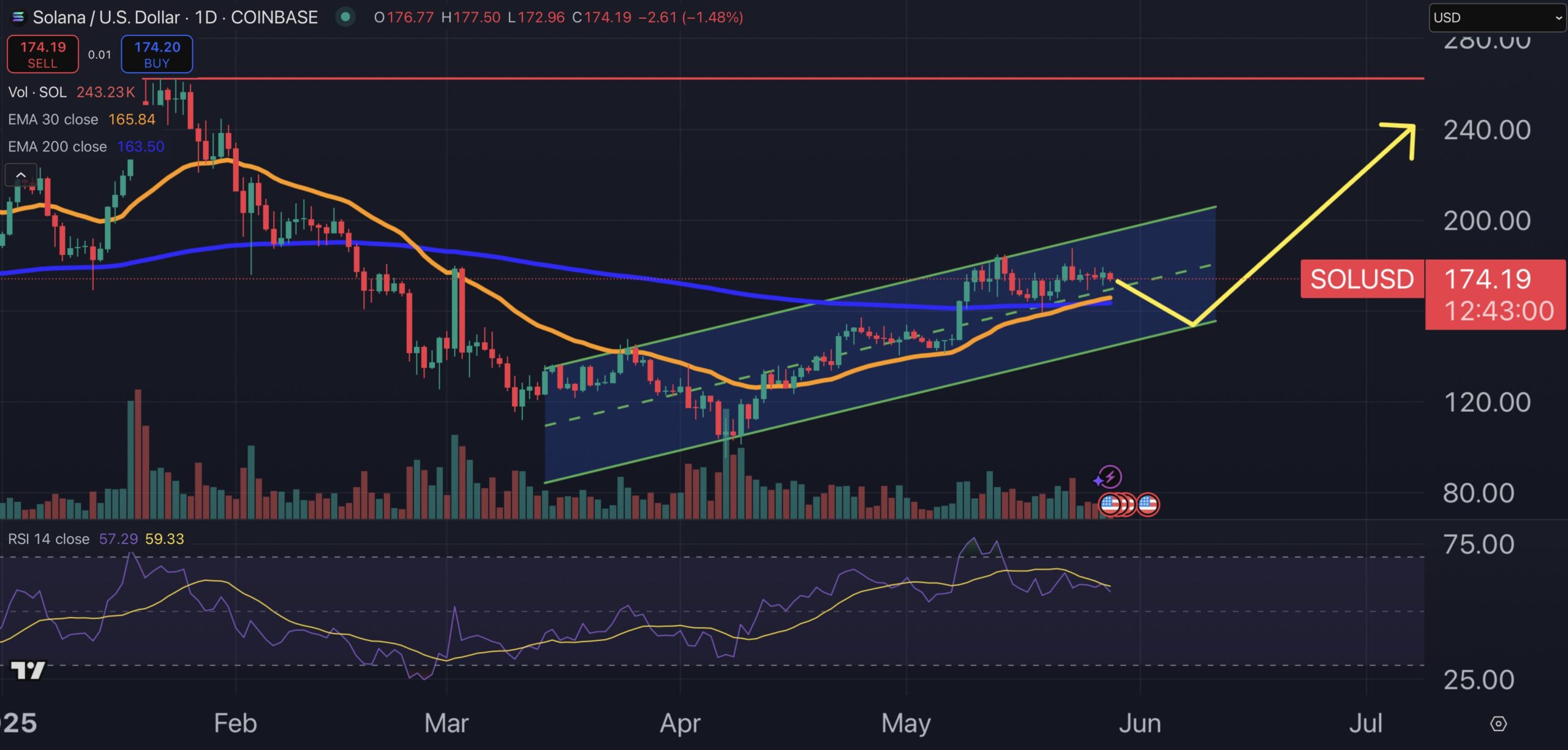
A global malware campaign has exposed more than 10 million people to deceptive crypto app ads, according to a new report from cybersecurity firm Check Point.
Key Takeaways:
- Fake crypto app ads have exposed over 10 million people to malware.
- The malware uses JavaScript and advanced evasion tactics to avoid detection.
- Victims risk losing passwords, Telegram data, and access to crypto wallets.
The campaign, which mimics nearly 50 popular crypto applications such as Binance, MetaMask, and Kraken, has been operating under the radar since at least March 2024.
Dubbed “JSCEAL” by Check Point Research, the operation deploys fake crypto app interfaces through online advertisements, luring users into downloading malware that siphons sensitive data.
Stealthy JavaScript Malware Evades Detection with Advanced Tactics
The malicious software leverages JavaScript and employs advanced evasion techniques, making it difficult to detect and analyze.
Check Point highlighted the role of social media platforms in enabling the campaign’s scale. Meta’s ad tools showed over 35,000 malicious advertisements were disseminated in just the first half of 2025.
While an estimated 3.5 million users in the European Union encountered these ads, Check Point noted the campaign also targeted users in Asia — regions where crypto trading and social media usage are particularly dense.
The firm stressed that estimating the precise number of infected devices remains difficult, given that ad impressions do not directly translate into malware infections.
Nonetheless, the campaign’s sophistication and broad targeting suggest the real impact could be much higher than initial estimates.
The malware tricks victims by presenting a website that closely resembles the real app’s homepage.
When users attempt to install what appears to be a legitimate application, a hidden malware installation runs in parallel.
The app often opens the actual platform’s interface to avoid suspicion, while stealing data in the background.
Once installed, the malware collects a wide range of personal information. This includes keystrokes, which can expose passwords, Telegram credentials, browser cookies, and even saved autofill data.
It also has the capability to manipulate crypto browser extensions like MetaMask, making it a significant threat to digital asset holders.
Check Point emphasized that the malware’s design relies heavily on obfuscation and compiled code, further complicating analysis.
The goal appears to be the extraction of as much device and user data as possible, sending it to threat actors likely seeking to monetize the information or breach users’ crypto wallets.
Study Reveals Widespread Leaks of Crypto Keys
A recent study has revealed the extent of sensitive information leaked through ransomware attacks and data breaches, including key financial documents and crypto keys.
The report, which analyzed over 141 million records from 1,297 breach incidents, revealed that cryptographic keys were stolen in 18% of the breaches.
Financial documents appeared in 93% of the breach incidents studied, accounting for 41% of all analyzed files.
Nearly half included bank statements, and over a third contained International Bank Account Numbers.
In 82% of the cases, customer or corporate personally identifiable information (PII) was exposed, much of it originating from customer service interactions.